Practicing the CBSE Sample Papers for Class 12 Informatics Practices Set 5 allows you to get rid of exam fear and be confident to appear for the exam.
CBSE Sample Papers for Class 12 Informatics Practices Set 5 with Solutions
Time : 3 hrs
Max. Marks : 70
General Instructions:
- This question paper contains five sections, Section A to E.
- All questions are compulsory.
- Section A have 18 questions carrying 01 mark each.
- Section B has 07 Very Short Answer type questions carrying 02 marks each.
- Section C has 05 Short Answer type questions carrying 03 marks each.
- Section D has 03 Long Answer type questions carrying 05 marks each.
- Section E has 02 questions carrying 04 marks each. One internal choice is given in Q35 against part c only.
- All programming questions are to be answered using Python Language only.
Section – A
Question 1.
A shareware is [1]
(a) free of cost
(b) freely available for a limited period
(c) has some restrictions for use
(d) Both (b) and (c)
Answer:
(d) Both (b) and (c)
Question 2.
Bulk volume of calls/messages from looking to be authorised sources is an example of [1]
(a) cyber stalking
(b) bullying
(c) IPR infringement
(d) phishing
Answer:
(d) phishing
![]()
Question 3.
The savefig( ) function [1]
(a) saves a DataFrame
(b) saves a Series
(c) saves a panel
(d) saves a graph
Answer:
(d) saves a graph
Question 4.
Open office is a/an ………… [1]
(a) documentation
(b) spreadsheet
(c) presentation
(d) office application suite
Answer:
(d) office application suite
Question 5.
Which of the following performs a pre-defined task and returns some type of result? [1]
(a) Database
(b) SQL function
(c) Implementation
(d) None of these
Answer:
(b) SQL function
Question 6.
Given a Series : [1]
nums=pd.Series([9,8,7,6,5],index=range(0,10,2))
nums[1:3]
Find the output of the given code.
(a) 2 8
(b) 4 7
(c)
2 8
4 7
(d)
2 8
6 7
Answer:
(c)
2 8
4 7
Question 7.
Which of the following is not an e-Waste?
(a) Books
(b) Laptop
(c) Monitor
(d) Motherboard
Answer:
(a) Books
Question 8.
Given the code:
datastud=[[‘Shreya’,20,30],[‘Rakhi’,23,50],[‘Priya’,45,90]]
dfs=pd.DataFrame(datastud)
The statement to add the column names ‘Name’,’Eng’,’IP’ to the DataFrame will be
(a) dfs.fie 1 ds = [ ‘Name’ , ‘ Eng’, ‘ IP’ ]
(b)dfs.rows= [ ‘Name’, ‘ Eng’, ‘ IP’ ]
(c) dfs . col umns=[ ‘ Name ’, ‘ Eng ’, ‘ IP ’ ]
(d) None of these
Answer:
(c) dfs . col umns=[ ‘ Name ’, ‘ Eng ’, ‘ IP ’ ]
![]()
Question 9.
A website is a collection of [1]
(a) web server
(b) web page
(c) web browser
(d) WWW
Answer:
(b) web page
Question 10.
Write the output of the following SQL query. [1]
SELECT INSTR(‘INTERNATIONAL’. ‘NA’ );
(a) 5
(b) 6
(c) 11
(d) 2
Answer:
(b) 6
Question 11.
The ……………. translates Internet domain and host names to IP address. [1]
(a) Domain Name System (DNS)
(b) Routing Information Protocol (RIP)
(c) Internet Relay Chart (IRC)
(d) Network Time Protocol (NTP)
Answer:
(a) Domain Name System (DNS)
Question 12.
Amita wants to display current date and time through following SQL statement. However, she is not getting the correct answer. [1]
SELECT DAY0FYEAR(‘2014-01-30’): .
Which of the following function will help her to get the desired output?
(a) TIME( )
(b) DATE( )
(c) CURDATE( )
(d) NOW( )
Answer:
(b) DATE( )
Question 13.
Which of the following proves a website to be authentic? [1]
(a) Padlock
(b) Digital certificate
(c) Starting with https://
(d) All of these
Answer:
(d) All of these
Question 14.
A table ”Transport” in a database has degree 3 and cardinality 8. What is the number of rows and columns in it? [1]
(a) 3,8
(b) 8,3
(c) 11,5
(d) 5,11
Answer:
(a) 3,8
Question 15.
What will be the order of sorting in the following MySQL statement? [1]
SELECT emp_id, emp_name from Employee order by emp_id,emp_name;
(a) Sorting {emp_id, emp_name}
(b) Sorting {emp_name, emp_id}
(c) Sorting {emp_id} but not emp_name
(d) None of these
Answer:
(a) Sorting {emp_id, emp_name}
Question 16.
Which SQL function will give ‘MAHAL’ as output in the following query? [1]
SELECT(UPPER(______(“Taj Mahal”,5));
(a) INSTR
(b) STRING
(c) MID
(d) SUB
Answer:
(c) MID
Question 17.
Assertion (A) Permission given to use a product by the copyright holder is license. [1]
Reason (R) One should not use the copyrighted product without taking license.
(a) Both A and R are true and R is the correct explanation of A.
(b) Both A and R are true but R is not the correct explanation of A.
(c) A is true but R is false.
(d) A is false but R is true.
Answer:
(a) Copyrights law gives the copyright holder a set of rights that they alone can avail legally. It prevents others from copying, using or selling the work. To use other’s copyrighted material, one needs to obtain a license from them.
Question 18.
Assertion (A) Sorting is the operation to arrange data in a specific order , sort_values ( ) function used to perform the operation. [1]
Reasoning (R) Row wise shorting cannot be performed in python dataframe objects.
(a) Both A and R are true and R is the correct explanation of A.
(b) Both A and R are ture and R is not the correct explanation of R .
(c) A is true but R is false.
(d) Both A and R are false.
Answer:
(c) The sort_values( ) function sorts a DataFrame by columns or by rows based on the value of its elements and returns the sorted DataFrame as a new DataFrame instance. Either rows are sorted (axis=0) or columns are sorted (axis=1). Column ordering and row ordering is to be specified through the parameter “by”.
Section – B
Question 19.
What do you mean by network topology? Write different types of topology. [2]
Or
Mr. Chandervardhan is not able to identify the domain name in the given URL. Identify and write it for him. Also, explain what is URL?
http ://www. cbsenic .in/aboutus. htm
Answer:
A network topology is the arrangement with which computer systems or network devices are connected to each other. Topologies may define both physical and logical aspect of the network. Both logical and physical topologies could be same or different in a same network.
There are different types of topology, which are as BUS, STAR, TREE, MESH.
Or
Domain in http://www.cbsenic.in/aboutus.htm is “www.cbsenic.in”. URL is the uniform resource locator which identifies address of each webpage on the www.
![]()
Question 20.
Which SQL function is used to remove leading and trailing spaces from a character expression X, where X = ‘LEARNING ###MYSQL####’ (# denotes a blank space) and also give the output of X. [2]
Answer:
TRIM function is used to remove all leading and trailing spaces from the given character expression.
Syntax TRIM(t(BOTH|LEADING|TRAILING) [remstr] FROM] str/column_name)
e.g. mysql > SELECT TRIM( ‘ LEARNING ##MYSQL###’);
OutputLEARNING###MYSQL
Spaces between ‘LEARNING’ and ‘MYSQL’ cannot be removed.
Question 21.
Which type of MySQL function accepts only numeric values? Give the name of some functions of that type. [2]
Answer:
Mathematical functions accept only numeric values and return the value of same type. These functions are used to perform mathematical operations on the database data.
Some mathematical functions are POW( )/POWER( ), ROUND( ), etc.
Question 22.
Write the Python code to create a Series with name flavours , having elements: Chocolate, Vanilla, Strawberry, Coffee and indexes as p,q,r and s, respectively. [2]
Answer:
flavours=pd.Series([‘Chocolate• ‘Vanilla’, ‘Strawberry’, ‘Coffee’],
index=[‘p’,‘q’,‘r’,‘s’])
print(flavours)
Question 23.
What do you mean by spyware? [2]
Or
What Cyber stalkers do to trouble their victims?
Answer:
Spyware is a type of malware that is installed on a computer without the knowledge of the owner in order to collect the owner’s private information. Spyware is often hidden from the user in order to gather information about Internet interaction, keystrokes, passwords and other valuable data.
Or
Cyber stalkers do the following to trouble their victims
- Uploading personal information such as name, address, social security number or phone number on the Internet.
- Hacking and saving E-mails, text messages and social media posts and using them to harass or blackmail a victim.
- Hacking into the victim’s social media account to post offensive material and comments.
- Using the victim’s social media account or E-mail to stalk and contact others.
- Creating malicious websites, fake social media profiles and blogs about a victim.
Question 24.
Given a DataFrame created as: [2]
import pandas as p
Stud=p.Series({‘Name’:[‘Ria’,‘Priya’,‘Jack’],‘Eco’:[56,67,89],‘IP’:[90,87,45],
‘Eng’:[58,78,32]})
Studdf=p.Data Frame(Stud)
print(Studdf[0:2])
What will be the output of the above code?
Answer:
When a range is specified while printing a DataFrame , it prints from start index to endindex -1. Given code prints rows 0, 1.
Name [Ria, Priya, Jack]
Eco [56, 67, 89]
Question 25.
Rama created a Series storing the names and prices-xif icecreams as follows : [2]
import pandas as pd …………
icecream=pd.Series([150,200,300],index=[‘Blackberry’,‘B1 ackforest’,‘Butter’])
Write the Python statements for the following:
(i) She wants to display the icecream prices increased by 30.
(ii) The command that displays the third row.
Answer:
(i) icecream+3D
(ii) print (icecream[2:])
Section – C
Question 26.
Mr. Manav, a database administrator in “Global Educational and Training Institute” has created following table named “Training” for the upcoming training schedule: [3]
Table: Training
| Training_Id | Name | Email_Id | Topic | City | Fee |
| ND01 | Mr. Rajan | raj@gmail. com | Cyber Security | New Delhi | 10000 |
| GU01 | Ms. Urvashi | urv@yahoo.com | ICT in Education | Gurugram | 15000 |
| FD01 | Ms. Neena | neenarediff.com | Cyber Security | Faridabad | 12000 |
| ND02 | Mr. Vinay | NULL | ICT in Education | New Delhi | 13000 |
| GU02 | Mr. Naveen | nav@gmail.com | Cyber Security | Gurugram | NULL |
Predict the output of the following queries:
(i) SELECT SUBSTR(City,2,4) FROM Training WHERE Topic <> ‘Cyber Security’:
(ii) SELECT NAME FROM Training WHERE INSTR (Emai1_ .Id, ‘@‘)=0;
(iii) SELECT Topic , COUNT!*) FROM Training GROUP BY Topic;
Answer:
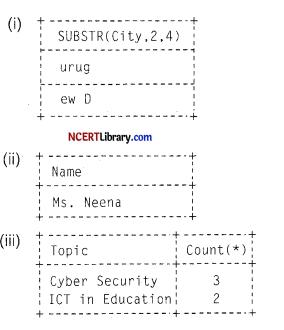
![]()
Question 27.
| Year | Month | Passengers |
| 2010 | Jan | 25 |
| 2010 | Mar | 50 |
| 2012 | Jan | 35 |
| 2010 | Dec | 55 |
| 2012 | Dec | 65 |
Write the code to create the above DataFrame: [3]
Answer:
import pandas as pd
data=i”Year”:[2010,2010,2012,2010,2012],”Month”:[“Jan”,”Mar”,”Jan”,”Dec”.”Dec”],
“Passengers”:[25.50,35,55,65])
df=pd.DataFrame(data)
print(df)
Question 28.
Consider the following DataFrame df: [3]
| Code | Name | Price | Qty | Discount |
| C1 | ABC | 5500 | 10 | 10 |
| C2 | XYZ | 4500 | 8 | 5 |
| C3 | PQR | 5200 | 12 | 8 |
| C4 | MNO | 3000 | 9 | 15 |
| C5 | LMN | 5500 | 11 | 12 |
(i) Write down the command that will give the following output.
| Code | C1 |
| Name | ABC |
| Price | 3000 |
| Qty | 8 |
| Discount | 5 |
dtype : object
(ii) Find the most repeat value of a given set of number of DataFrame.
(iii) To sort the index label of DataFrame df in descending order.
Answer:
(i) print(df .min(axis=1))
(ii) print(df .mode( ))
(iii) print(df.sort_index(ascending=Fa1se))
Question 29.
Abhishek uses computer and mobile for his personal use. Study the following cases and answer the questions given below. [3]
(a) Once he got the message in Whatsapp that CBSE is announcing the result of class XII tomorrow at 12:00 pm. lie forwarded the message to his few friends. But later he came to know that no such announcement was there in CBSE official web-site. In this case he violated …………..
(b) He is getting abuse messages from an unknown number due to which he is thinking of quarreling with that person. The unknown person can be called as …………….
(c) He registered himself in one website by giving his email id and phone number he is leaving ……….
Or
Write some symptoms of a malware attack.
Answer:
(a) Communication etiquettes
(b) Internet troll
(c) Digital footprints
Or
Some primary indications of a malware attack are :
(i) A program disappears from that computer even though you did not intentionally remove the program.
(ii) An antivirus program cannot be installed on the computer, or the antivirus program will not run.
(iii) You see unusual error messages.
(iv) You cannot print items correctly.
Question 30.
Shanya Kumar is working with the following table Customers: [3]
Table: Customers
| CNO | CNAME | CITIES |
| C1 | SANYAM | DELHI |
| C2 | SHRUTI | DELHI |
| C3 | MEHER | MUMBAI |
| C4 | SAKSHI | CHENNAI |
| C5 | RITESH | INDORE |
| C6 | RAHUL | DELHI |
| C7 | AMEER | CHENNAI |
| C8 | MINAKSHI | BANGLORE |
| C9 | ANSHUL | MUMBAI |
Write the queries for the following:
(i) To display the city names in lower case letter whose CNO is either C5 or C9.
(ii) To display the length of Customer’s name for those Customers whose NAME end with R or L.
(iii) To display the Customer’s name and their respective CITIES merged together for all the Customers whose CNO is ending with 8.
Or
What is the differences between HAVING clause and WHERE clause?
Answer:
(i) mysql>SELECT LOWER(CITIES)FROM Customers WHERE CN0 =‘C5’ OR CN0 =‘C9’;
(ii) mysql >SELECT LENGTH(CNAME) FROM Customers WHERE CNAME LIKE ‘%R’ OR CNAME LIKE ‘SSL’;
(iii) mysql >SELECT C0NCAKCNAME,CITIES) FROM Customers WHERE CN0 LIKE ‘%8’ ;
| WHERE clause | HAVING clause |
| WHERE clause is used to filter the records from the table based on the specified condition. | HAVING clause is used to filter record from the groups based on the specified condition. |
| WHERE clause implements in row operation. | HAVING clause implements in column operation. |
| WHERE clause cannot contain aggregate function. | HAVING clause can contain aggregate function. |
| WHERE clause can be used with SELECT, UPDATE, | HAVING clause can only be used with SELECT |
| DELETE statement. | statement. |
| WHERE clause is used with single row functions like UPPER, LOWER etc. | HAVING clause is used with multiple row functions like SUM, COUNT etc. |
Section – D
Question 31.
Consider the following table Graduate and write SQL commands for (i) to (v). [5]
Table : Graduate
| Name | Stipend | Subject | Average | Div |
| Karan | 400 | Physics | 68 | 1 |
| Divakar | 450 | Computers | 68 | 1 |
| Divya | 300 | Chemistry | 62 | 2 |
| Arun | 350 | Physics | 63 | 1 |
| Sabina | 500 | Mathematics | 70 | 1 |
| John | 400 | Chemistry | 55 | 2 |
| Robert | 250 | Physics | 64 | 1 |
| Rubina | 450 | Mathematics | 68 | 1 |
| Vikas | 500 | Computers | 62 | 1 |
| Mohan | 300 | Mathematics | 57 | 2 |
(i) List the Names of those students who obtained Div 1.
(ii) Display a report, listing Name , Stipend , Subject and amount of stipend received in a year assuming that the Stipend is paid every month.
(iii) Display first three characters of student Name where/whose SNo is 7.
(iv) Display the student Names having 2nd division.
(v) Display division wise Name of students in alphabetical order.
Or
Write the short note on :
(i) DAYOFWEEK( )
(ii) DAYOFYEAR( )
(iii) POWER( )
(iv) MOD( )
(v) SUBSTR( )
Answer:
(i) SELECT Name FROM Graduate WHERE Div=1;
(ii) SELECT Name, Stipend, Subject, Stipend *12 FROM Graduate;
(iii) SELECT LEFT(NAME,3)FROM Graduate WHERE SN0=7;
(iv) SELECT NAME FORM Graduate WHERE Div=2;
(v) SELECT Div.Name FROM Graduate GROUP BY Div ORDER BY Name;
Or
(i) DAYOFWEEK( ) This function returns the week day number (1 = Sunday, 2= Monday, ,7 = Saturday) for a date specified as an argument.
(ii) DAYOFYEAR ( ) This function returns day of the year for a given date in numeric format. The return value is within the range of 1 to 366.
(iii) POWER( ) function returns the value of a number raised to the potfver of another number.
(iv) MOD( ) function returns the remainder of a number dividing by another number.
(v) SUBSTR( ) function extracts certain number of characters from a start position and number of characters specified.
![]()
Question 32.
A company in Mega Enterprises has 4 wings of buildings as shown in the diagram : [5]
Centre to centre distances between various buildings:
W3 to W1 – 50m
W1 to W2 – 60m
W2 to W4 – 25m
W4 to W3 – 170m
W3 to W2 – 125m
W1 to W4 – 90m
Number of computers in each of the wing:
W1 – 150
W2 – 15
W3 – 15
W4 – 25
Computers in each wing are networked but wings are not networked. The company has now decided to connect the wings also.
(i) Suggest a most suitable cable layout for the above connections.
(ii) Suggest the most appropriate topology of the connection between the wings.
(iii) Suggest the placement of the following devices with justification, if the company wants minimized network traffic.
(a) Repeater
(b) Hub/Switch
(iv) Expand the following terms:
(a) HTTP
(b) TCP/IP
(v) Suggest the suitable wing to house the server.
Answer:
(i) Most suitable layout according to distance is :
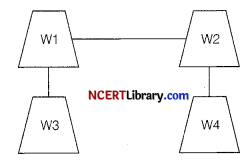
(ii) Star topology
(iii) (a) Repeaters may be skipped as per above layout (because distance is less than 100 m). (b) In every wing
(iv) (a) Hyper Text Transfer Protocol
(b) Transmission Control Protocol/Internet Protocol
(v) Wing W1 is best to house the server because it has maximum number of computers.
Question 33.
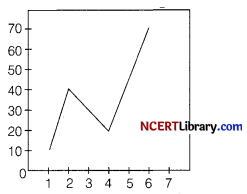
Consider the following graph. Write the code to plot it.
Or
Draw the following bar graph representing the guantity of items in each month
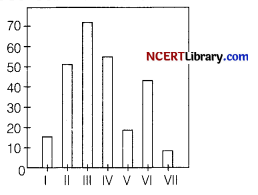
Answer:
from matplotlib import pyplot as plt
x=[1,2,4,6]
y= [10,40,20,70]
plt.plot(x.y)
plt. ti11e(” Line graph”)
plt.ylabel(‘Y axis’)
plt. x1abel(’X axis’)
pit.show( )
Or
from matplotlib import pyplot as plt
x=[‘I’,’II’,’III’,’IV’,’V’,’VI’ , ’ VII’ ]
y=[10,50,70,60,20,50,10]
plt.bar(x,y)
plt.title(“Line graph”)
plt,ylabel(‘Y axis’)
plt.xlabel(‘X axis’ )
plt.show( )
Section – E
Question 34.
Mr. Krishnamurthy, who is a new user of Python Pandas, has created the following Series “Electrical” carrying names of electrical appliances as values and their wattage as the index. He wants to perform certain operations on the Series . You are supposed to help him in writing the commands: [1+1+2]
Electrical
| Index | Name |
| 12 W | LED |
| 200 W | Fan |
| 1000 W | Electric Iron |
| 1200 W | Rice Cooker |
(i) He wants to change the index of Electrical series ”LED” element to “PL’.
(ii) To display the record of ‘Fan”.
(iii) Remove dataset with index 1000 W
Or (Option for part (iii) only)
Display the last rows of the dataset.
Answer:
(i) Electrical=Electrical . rename(index={‘ 12W ’ : “A” })
(ii) Electrical [Electrical ==“Fan”]
(iii) del Electrical [‘‘1000 W”]
Or
Print(Electrical[ -1: ]
Question 35.
Consider the following table named “Product”, showing details of products being sold in a grocery shop. [1+1+2]
Table: Product
| PCode | PName | UPrice | Manufacture |
| P01 | Washing Powder | 120 | Surf |
| P02 | Tooth Paste | 54 | Colgate |
| P03 | Soap | 25 | Lux |
| P04 | Tooth Paste | 65 | Pepsodent |
| P05 | Soap | 38 | Dove |
| P06 | Shampoo | 245 | Dove |
Write SQL queries for the following and output(s) produced by executing the following queries on the basis of the information given above in the table Product.
(i) Create the table Product with appropriate data types and constraints.
(ii) Identify the PRIMARY KEY in table Product.
(iii) List the Product Code, product Name and Price in with their Product Name for all Dove Manufacture.
Or (Option for part (iii) only)
Increase the Price by 12 per cent for all the products manufactured by Dove.
Answer:
(i) CREATE TABLE Product(
PCode char(3) PRIMARY KEY,
PName varchar(25) NOT NULL,
UPrice int(4),
Manufacture varchar(30));
(ii) PCode
(iii) SELECT PCode, PName, UPrice FROM Product WHERE Manufacture=”Dove”;
Or
UPDATE Product SET UPrice =UPrice+0.12*UPrice WHERE Manufacture=”Dove”;