Practicing the CBSE Sample Papers for Class 10 Computer Applications Set 9 allows you to get rid of exam fear and be confident to appear for the exam.
CBSE Sample Papers for Class 10 Computer Applications Set 9 with Solutions
Maximum Marks: 50
Time Allowed: 2 hours
General Instructions:
- This Question Paper has 5 Sections A-E.
- All Questions are compulsory. However, an internal choice of approximately 30% is provided.
- Section A has 12 questions carrying 01 mark each.
- Section B has 7 Very Short Answer (VSA) type questions carrying 02 marks each.
- Section C has 4 Short Answer (SA) type questions carrying 03 marks each.
- Section D has 1 Long Answer (LA) type question carrying 04 marks.
- Section E has 2 Source based /Case-based /Passage based Questions carrying 04 marks each.
Section – A
(All Questions are Compulsory) [1 mark]
Question 1.
The right to control your own personal information is the right of:
(A) access.
(B) security.
(C) privacy.
(D) None of the above.
Answer:
(C) privacy.
Explanation: The right to control your own personal information is the right of privacy.
Question 2.
Which of this is not a constituent of residential telephone line?
(A) A high-speed downstream channel
(B) A medium-speed downstream channel
(C) A low-speed downstream channel
(D) An ultra-high speed downstream channel
Answer:
(C) A low-speed downstream channel
Explanation: A low-speed downstream channel is not a constituent of a residential telephone line. But it might be just a two-way telephone channel. Internet can be provided through a high-speed downstream channel in a residential telephone line.
![]()
Question 3.
What is the secured version of File Transfer Protocol?
(A) EFTP
(B) SFTP
(C) SMTP
(D) EMTP
Answer:
(B) SFTP
Explanation: Secure shell file transfer protocol (SSH FTP or SFTP) and file transfer protocol secure (FTP over TLS/SSL or FTPS) enable secure file transfer using two distinct communication mechanisms.
Question 4.
When collection of various computers seems a single coherent system to its client, then it is called
(A) Computer network
(B) Distributed system
(C) Networking system
(D) Mail system
Answer:
(B) Distributed system
Explanation: A Computer network is defined as a collection of interconnected computers which uses a single technology for connection. A distributed system is also the same as computer network but the main difference is that the whole collection of computers appears to its users as a single coherent system.
Example: World wide web
Question 5.
In computer network nodes are
(A) The computer that originates the data
(B) The computer that routes the data
(C) The computer that terminates the data
(D) All of the mentioned
Answer:
(D) All of the mentioned
Explanation: In a computer network, a node can be anything that is capable of sending data or receiving data or even routing the data to its destination. Routers, Computers and Smartphones are some examples of network nodes.
Question 6.
CDMA uses ______ waves.
(A) Radio
(B) Micro
(C) Infrared
(D) Electromagnetic
Answer:
(D) Electromagnetic
Question 7.
Which character is used to represent when a tag is closed in HTML?
(A) #
(B) !
(C) /
(D) \
Answer:
(C) /
Explanation: The forward-slash (/) is used to indicate the closure of a tag within HTML.
Question 8.
Among the following, which is the HTML paragraph tag?
(A) <p>
(B) <pre>
(C) <hr>
(D) <a>
Answer:
(A) <p>
Explanation: <p> tag is used for paragraph in HTML.
Question 9.
In HTML, which attribute is used to create a link that opens in a new window tab?
(A) src=”_blank”
(B) alt=” blank”
(C) target=”_self”
(D) target=”_blank”
Answer:
(D) target=”_blank”
Explanation: Add the target=”_blank” attribute in the Anchor tag. target=”_blank” attribute makes a link open in a new window tab.
![]()
Question 10.
Which of the following HTML tag is used to create an unordered list?
(A) <ol>
(B) <ul>
(C) <li>
(D) <U>
Answer:
(B) <ul>
Explanation: <ul> tag is used to create the unordered list items in an HTML document. By default, unordered list items will display in a bulleted format.
Different types of unordered list Attribute Values are:
Disc
Circle
Square
Syntax: <ul> Unordered List Items </ul>
Questions No-11 & 12 are Assertion and Reason types. Each question consists of two statements, namely, Assertion (A) and Reason (R). Select the most suitable option considering the Assertion & Reason. DIRECTIONS: In each of the questions given below, there are two statements marked as Assertion (A) and Reason (R). Mark your answer as per the codes provided below:
(A) Both A and R are true and R is the correct explanation of A.
(B) Both A and R are true but R is not the correct explanation of A.
(C) A is true but R is false.
(D) A is false but R is true.
(E) Both A and R are false.
Question 11.
Assertion (A): The “autoplay” attribute of <audio> Tag.
Reason (R): The “autoplay” specifies that the audio will start playing as soon as it is ready.
Answer:
(A) Both A and R are true and R is the correct explanation of A.
Question 12.
Assertion (A): The word anchor has come from the function performed by anchor in a ship.
Reason (R): An anchor element is used to create a Table in a webpage.
(A) Both A and R are true and R is the correct explanation of A.
(B) Both A and R are true but R is not the correct explanation of A.
(C) A is true but R is false.
(D) A is false but R is true.
(E) Both A and R are false.
Answer:
(C) A is true but R is false.
Section – B
[2 marks]
Question 13.
What are the limitations of e-learning?
Answer:
E-Learning requires strong self-motivation and time management skills. Lack of self-motivation among students continues to be one of the primary reasons why students fail to complete online courses. In traditional classrooms, there are numerous factors which constantly push students towards their learning goals.
Question 14.
Harita wants to learn about e-business. Help her understand it by writing two important features of e-business. Give two most commonly used e-business sites.
OR
What are the effects of online learning on students?
Answer:
- Offers opportunity to access new markets across the globe.
- Allows 24 × 7 access to firm’s products and services.
Two most commonly used e-business sites are Amazon and Flipkart.
OR
Online learning has helped students to become independent learners before they make their way into the real world. Students got opportunities to explore new learning applications and platforms during the class, which helped them to develop new skills and capabilities accelerating their growth trajectory.
![]()
Question 15.
How do we insert audio in an HTML file?
Answer:
<!DOCTYPE html>
<html>
<head>
<title> INSERT SOUND FILE </title> </head>
<body>
<h2> LISTENING TO MUSIC </h2>
<audio controls=”controls” src=”C:\ Vodafone\Podcast\Music.mp3″> </audio>
</body>
</html>
Question 16.
Name fundamental requisites that ensure safe electronic transactions and payments.
OR
What do you mean by copyleft licences.
Answer:
SECURITY REQUIREMENTS
- Authentication of merchant and consumer.
- Confidentiality of data.
- Integrity of data.
- Non-repudiation.
OR
Copyleft is a general method for making a program (or other work) free (in the sense of freedom, not “zero price”), and requiring all modified and extended versions of the program to be free as well. … So instead of putting GNU software in the public domain, we “copyleft” it.
Commonly Made Error:
Some candidates found it difficult to provide an appropriate need of computer network. Mostly candidates write definition or advantages instead of needs.
Answering Tip:
Students should have sufficient knowledge about computer networks. They should write the needs in point.
Question 17.
Explain the general CSS nomenclature.
Answer:
In CSS, the styling commands are written in value and property fashion. CSS includes a system terminator- semicolon. The entire style is wrapped in curly braces and attached to the selector. This creates a style sheet that can be applied to an HTML page.
Commonly Made Error:
Students get confused between inline and external css.
Answering Tip:
Students must learn and understand the concept of inline and external css.
Question 18.
What is the difference between container tag and empty tag?
OR
Rani is a student of Class X, wants to represent a list in webpage. Create an ordered list of the name of the subjects you study in school.
Answer:
A container tag has both the start and the end tag. The text or the graphic is inserted inside the beginning and end tag of the container tag. For example: <body>. This is a container tag</body>. The<BODY> tag here is a container tag which has both the beginning and the ending tag and the text is between both the tags.
The empty tag is a stand-alone tag. This implies that such a tag has beginning but no ending tag. For example: The <BR> tag is used for adding one line break. Such a tag does not need an end so as to tell the browser, that end of line break has come because there is no need. Such a tag is called empty tag.
OR
<ol>
<li> English</li>
<li> Mathematics</li>
<li> Science </li>
<li> Social Science </li>
</li> Bengali </li>
</ol>
Question 19.
Differentiate between the Border and Bordercolor attributes of the <TABLE> tag.
Answer:
Border: This attribute draws a border around the table. It specifies the width of the border of a table. If a table border is not given or its value is zero, then no border will be displayed there.
Bordercolor: This attribute is used to set the border color of a table. The default color of the border is gray, but we can change it by assigning different color name to Bordercolor attribute.
Commonly Made Error:
Students get confused between colour and color.
Answering Tip:
Color is the spelling used in the United States. Colour is used in other English-speaking countries.
Section – C
[3 marks]
Question 20.
How many types of plagiarism? Is plagiarism a form of stealing?
Answer:
Plagiarism has various types:
- Direct plagiarism
- Mosaic plagiarism
- Self plagiarism
- Accidental plagiarism
Plagiarism is an act of fraud. It involves both stealing someone else’s work and lying about it afterward. But can words and ideas really be stolen? According to U.S. law, the answer is yes.
![]()
Question 21.
Write a short note on Video Conferencing.
Answer:
Video conferencing is a communications technology that integrates video and audio to connect users anywhere in the world as if they were in the same room. This term usually refers to communication between three or more users who are in at least two locations, rather than csne on-one communication, and it often includes; multiple people at each location.
Each user or group of users who are participating in a video conference typically must have a computer, a camera, a microphone, a video screen and a sound system. Another requirement is a connection to the communications system that is being used, which in the 21st century usually is the Internet but might also be a satellite-based system, a broadcast signal or other communications technology.
Advantages:
- When using video conferencing, participants can see and hear each other in real time or close to it, allowing natural face-to-face conversations and visual elements; that are not possible with voice-only communications technology.
- It saves time and money
Disadvantages:
- Expensive
- Lack of familiarity with technology can cause frustration.
Question 22.
What is the difference between inline, inline-block, and block?
OR
Why is it important to test the webpage in different browsers?
Answer:
Block Elements are <div> and <p>. They usually start on a new line and tan take space for an entire row or width.
Inline elements are <a>, <span>, <strong>, and <img> tags. They don’t start on a new line. However, they appear on the same line as the content and tags beside’ them. Inline block elements have padding and margins and set height and width values. Though, they are similar to inline elements.
OR
Yes, it is the most crucial thing or the most important trial to do when you design a webpage for the first time and make changes to it. Testing your website periodically in different browsers will help you make every webpage compatible with it as browsers have been going through many updates.
Question 23.
Mr. Ayus wants to transfer money online. You, being his friend explain the concept of Secure Electronic Transaction.
Answer:
Secure Electronic Transaction is a secure protocol developed by Master Card and Visa in collaboration. Theoretically, it is the best security protocol. It has the following componehts.
Card Holder’s Digital Wallet Software : Digital Wallet allows the card holder to make secure purchases online via point and click interface. Merchant Software: This software helps merchants to communicate Withj potential customers and financial institutions in a secure manner.
Payment Gateway Server Software : Payment gateway provides automatic and standard payment process. It supports the process for merchant’s certificate request.
Certificate Authority Software : This software is used by financial institutions to issue digital certificates to card holders and merchants, and to enable them to register their account agreements for secure electronic commerce.
Section – D
[4 marks]
Question 24.
Write the HTML code to design the web page as shown below, considering the specifications that follow. You can write code for any 4 specifications out of the given 5 specifications:
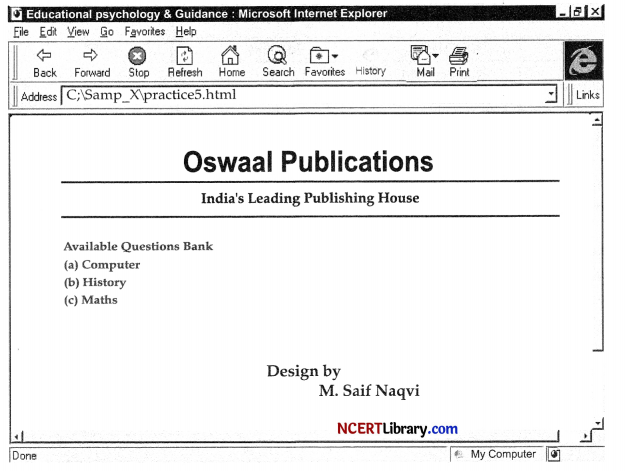
(a) Specification 1: Title is Oswaal Publications.
(b) Specification 2: Text colour is red and visited link colour is pink.
(c) Specification 3: Maximum size will be use for heading “Oswaal Publications”.
(d) Specification 4: Size of rest of text is 7 and the title “computer, history and maths” will be in ordered list.
(e) Specification 5: There are two horizontal lines in the web page.
OR
Sunny is a student, he wants to understand the tags used web in a webpage. Be carefully studying the webpage given below. Help him to Identify 8 tags that have been used in creating this webpage and write the usage of each of them.
This website is a gateway to film reviews. Following is a list of the top 5 films running successfully in cinema halls in September 2011.

Answer:
<HTML>
<HEAD> <TITLE> Oswaal Publications </TITLE> </HEAD>
<Body text = “red” vlink = “pink”> <center>
<H1> Oswaal Publications </H1>
<H1> size = “10” color = “black”>
<H4> India’s
Leading Publication House </H4>
<HR size = “10” color = “black”>(e)
</ center>
<Font size = “7”>
<OL type = “a”>
<B> Available Questions Bank
</B>
<LI> <A href = “Naqvi. htm”> Computer </A>
</LI> <LI>
<A href = “Saif.htm”> History </A> </ LI >
<LI >
<A href = “Maths, htm”> Maths </A> </ LI> </
< / OL>
<BR> <BR> <BR> <BR> <center> Design by <BR> M. Saif Naqvi </center> </Font> </Body>
</HTML>
OR
Following are the 10 tags that are used to create the preceding Web page along with their one line description:
(a) <HTML> : Refers to a structural tag that is used to mark the starting and ending of an HTML document. It ends with </HTML>.
(b) <BODY> : Refers to a structural tag that contains all the visible content, such as text, images, and link of a webpage. It ends with </BODY>
(c) <P> : Refers to a formatting tag that is used to begin a new paragraph. It ends with </P>
(d) <B> : Refers to a formatting tag that is used to boldface text in an HTML document. It ends with </B>.
(e) <CENTER> : Refers to a formatting tag that centralises the text on a Web page. It ends with </ CENTER>.
(f) <H1> : Refers to a formatting tag that is used to mark text as largest heading. It ends with </ HI >.
(g) <IMG> : Refers to a formatting tag that inserts inline images on a Web page.
(h) <OL> : Refers to a formatting tag that inserts numbered lists. It ends with </OL>.
(i) <LI> : Refers to a formatting tag that marks the list items in a numbered list. It ends with </LI>.
(j) <A> : Refers to a formatting tag that inserts hyperlink on a Web page. It ends with </A>.
Section – E
Case Study-1 [4 marks]
Question 25.
Ayus went to an interview for the post of web developer. In the technical test, he was supposed to design an HTML table as given below. Help him to complete the table with the right statements in the blanks. Observe the table and attempt any four questions (out of 5) given after the table.
| NAME | SUBJECT | MARKS |
| Hillary | aligned | 75 |
| Advanced Web | 60 | |
| Lary | Operating System | 80 |
| Advanced Web | 75 | |
| Total Average: 72.5 | ||
<table>
<tr>
<th>Name</th>
<th>Subject</th>
<th>Marks</th>
</tr>
<tr>
<td ______ = “2”>Hillary</td> <!-STATEMENT-1>
<td>Advanced Web</td>
<td>75</td>
</tr>
<tr>
<td>Operating Syatem</td>
<td>60</td>
<______> : <!-STATEMENT-2>
<tr>
<td rowspan = “2”>Lary</td>
<td>Advanced Web</td>
<td>80</td>
</tr>
<tr>
<______>Opeirating Syatem</td> <!-STATEMENT-3>
<td>75</td>
</tr>
<tr>
<tdx/td>
<td ______ = “3 ” >Total Average: 72.5</td> <!- STATEMENT – 4 >
</tr> :
<______> : <!-STATEMENT-5>
(a) Write the attribute value to complete Statement-1 to achieve the output given in the above table.
(b) Write suitable tag for the blanks given in Statement-2.
(c) Write the appropriate answer for the blank given in Statement-3
(d) Write the appropriate answer for the blank given in Statement-4
(e) Write the appropriate answer for the blank given in Statement-5
Answer:
(a) rowspan
(b) </tr>
(c) <td>
(d) colspan
(e) </table>
Case Study-2
Question 26.
In July 2020, several Twitter employees became victims of spear phishing attacks enabling the malicious actors to access the administrator’s tools. Malicious actors posed as Twitter IT administrators and emailed/phoned Twitter employees working from home, asking them to share user credentials. Using these compromised accounts, the cyber adversaries gained access to the administrator’s tools. It enabled them to reset the Twitter accounts of celebrities like Elon Musk, Barack Obama, Jeff Bezos, Apple, Uber, and many more to tweet scam messages asking for Bitcoin contributions.
As these celebrity accounts have a massive following, many Twitter users transferred at least $180,000 in Bitcoins to scam accounts. Luckily, the scam messages were published and noticed by the press. It forced Twitter to take immediate action. Based on the given information, answer the questions given below. Attempt any four questions:
(a) Identify the type of cybercrime
(b) Why is it called phishing?
(c) What are 4 types of phishing?
(d) Email authentication can help protect against phishing attacks. True or False?
(e) Why is understanding the risk of Phishing important?
Answer:
(a) phishing
(b) Analogous to fishing, phishing is also a technique to “fish” for usernames, passwords, and other sensitive information, from a “sea” of users. Hackers generally use the letter “ph” instead of “f” and therefore initially they were known as phreaks.
(c) Types of Phishing Attacks
- Spear Phishing.
- Whaling.
- Smishing.
- Vishing.
(d) True
(e) Phishing attacks are a constant threat to campus and are becoming increasingly sophisticated. Successful Phishing attacks can:
Cause financial loss for victims Put their personal information at risk Put university data and systems at risk