Practicing the CBSE Sample Papers for Class 10 Computer Applications Set 5 allows you to get rid of exam fear and be confident to appear for the exam.
CBSE Sample Papers for Class 10 Computer Applications Set 5 with Solutions
Maximum Marks: 50
Time Allowed: 2 hours
General Instructions:
- This Question Paper has 5 Sections A-E.
- All Questions are compulsory. However, an internal choice of approximately 30% is provided.
- Section A has 12 questions carrying 01 mark each.
- Section B has 7 Very Short Answer (VSA) type questions carrying 02 marks each.
- Section C has 4 Short Answer (SA) type questions carrying 03 marks each.
- Section D has 1 Long Answer (LA) type question carrying 04 marks.
- Section E has 2 Source based /Case-based /Passage based Questions carrying 04 marks each.
Section – A
(All Questions are Compulsory) [1 mark]
Question 1.
Intellectual property does not include-
(A) Creation of mind
(B) Artistic work
(C) Literary
(D) None of these
Answer:
(D) None of these
Question 2.
The length of an IPv6 address is?
(A) 32 bits
(B) 64 bits
(C) 128 bits
(D) 256 bits
Answer:
(C) 128 bits
Explanation: An IPv6 address is 128 bits long, which has 2^128 address space.
![]()
Question 3.
The term IANA stands for?
(A) Internet Assigned Numbers Authority
(B) Internal Assigned Numbers Authority
(C) Internet Associative Numbers Authoritative
(D) Internal Associative Numbers Authority
Answer:
(A) Internet Assigned Numbers Authority
Explanation: The term IANA stands for Internet Assigned Numbers Authority.
Question 4.
The term IPv4 stands for?
(A) Internet Protocol Version 4
(B) Internet Programming Version 4
(C) International Programming Version 4
(D) None of these
Answer:
(A) Internet Protocol Version 4
Explanation: The term IPv4 stands for Internet Protocol Version 4.
Question 5.
An email address is made up of:
(A) Four parts
(B) Two parts
(C) Single part
(D) Three parts
Answer:
(B) Two parts
Explanation: A valid email address is an address composed of two parts, a username and a domain name.
Question 6.
The Information Village is a programme of:
(A) M.S. Swaminathan Research Foundation
(B) Sarva Shiksha Abhiyan
(C) Ministry of IT
(D) None of the above
Answer:
(A) M.S. Swaminathan Research Foundation
Explanation: M.S. Swaminathan Research Foundation.
Question 7.
Which of the following HTML element is used for canvas graphics?
(A) <css>
(B) <paint>
(C) < canvas >
(D) < graphic >
Answer:
(C) < canvas >
Explanation: CSS i.e. Cascading Style Sheet is a scripting language. Canvas graphics are introduced in HTML5. Element used for canvas graphics is < canvas >. The HTML canvas element is used to draw graphics, on the fly, via scripting (usually JavaScript).
Question 8.
Which tag do we use in HTML for inserting a line-break?
(A) <a>
(B) <br>
(C) <b>
(D) <pre>
Answer:
(B) <br>
![]()
Question 9.
How to create a hyperlink in HTML?
(A) < a link = “www.thinkandlearn.com”> thinkandlearn.com </a>
(B) <a> www.thinkandlearn.com <thinkandlearn.com/a>
(C) <a href = “www.thinkandlearn.com”> thinkandlearn.com </a>
(D) <a url = “www.thinkandlearn.com” thinkandlearn.com/a >
Answer:
(C) <a href = “www.thinkandlearn.com”> thinkandlearn.com </a>
Explanation: <a href = “www.thinkandlearn.
com”> thinkandlearn.com </a>
Question 10.
In HTML, how do we insert an image?
(A) <img src = “jtp.png”/>
(B) <imghref = “jtp.png”/>
(C) <imglink = “jtp.png”/>
(D) <imgurl = “jtp.png”/>
Answer:
(A) <img src = “jtp.png”/>
Questions No-11 & 12 are Assertion and Reason types. Each question consists of two statements, namely, Assertion (A) and Reason (R). Select the most suitable option considering the Assertion & Reason. DIRECTIONS: In each of the questions given below, there are two statements marked as Assertion (A) and Reason (R). Mark your answer as per the codes provided below:
(A) Both A and R are true and R is the correct explanation of A.
(B) Both A and R are true but R is not the correct explanation of A.
(C) A is true but R is false.
(D) A is false but R is true.
(E) Both A and R are false.
Question 11.
Assertion (A): HTML is case sensitive language.
Reason (R): HTML is use to create WebPages.
Answer:
(B) Both A and R are true but R is not the correct explanation of A.
Question 12.
Assertion (A): <HR> tag is used for line break.
Reason (R): <HR> tag is a container tag.
Answer:
(E) Both A and R are false.
Section – B
[2 marks]
Question 13.
What is difference between online shopping and offline shopping?
Answer:
Offline shopping is the traditional way of shopping being present at the counter or shop or store. While online shopping is buying anything through the internet from your house.
Question 14.
What are the advantages of online transaction?
OR
What are the challenges in online transactions?
Answer:
Benefits of Online Transactions
- Providing practical payment system.
- Reducing human resources’ need.
- Providing a sense of security for consumers.
- Reaching a wider range of consumers.
- Doing easier promotion.
- Increasing customer retention rate.
- Providing fast and easy integration.
OR
- Low internet bandwidth.
- How to overcome low internet bandwidth issues.
- Card data security.
- How to overcome card data security issues.
- Technical integration.
- How to ensure a smooth payment gateway technical integration.
- Multi-currency transactions.
Question 15.
What is an colspan and bordercolor attributes in HTML?
Answer:
The colspan attribute in HTML specifies the number of columns a cell should span. The border-color property sets the color of an element’s four borders. This property can have from one to four values. If the border-color property has four values: border-color: red green blue pink; top border is red.
Question 16.
What is the CSC Digital Seva portal? What types of services are provided by the CSC Digital Seva portal?
OR
What is proprietary software? What are 3 examples of proprietary software?
Answer:
Common Service Centre or CSC Digital Seva portal is a digital platform that allows you to pay for specific services. The digital portal of CSC provides different types of services like educational, financial, health, skill, etc
OR
Proprietary software (sometimes referred to as closed source software) is software that legally remains the property of the organisation, group, or individual who created it.
Examples of proprietary software include: Windows and OS X operating systems.
Microsoft Office productivity suite.
Adobe Creative Suite productivity software.
Logic music creation software. paid-for games for consoles.
![]()
Question 17.
What is INPUT tag?
Answer:
INPUT tag is used to provide an input field in a form where the user can enter the data. An input field may be a textfield, a checkbox, a radio button, a button, and more. INPUT element is always used within the FORM element. Thus, INPUT element defines an object on the FORM which can receive user’s input.
Question 18.
Mention all the attributes of check box.
OR
Where to write CSS code?
Answer:
Attributes of checkboxes:
NAME: It adds an internet name to the field so the program that handles the form can identify the fields.
VALUE: It defines what will be submitted if checked.
ALIGN: It defines how the text field will be aligned form.
Valid Entries are : TOP, MIDDLE, BOTTOM, RIGHT, LEFT TEXTTOP, BASELINE, ABSMIDDLE, ABSBOTTOM.
TABINDEX: It defines in which order the different fields should be activated when the visitor clicks the tab key.
OR
Usually, CSS is written in a separate CSS file (with file extension . css ) or in a <style> tag inside of the <head> tag, but there is a third place which is also valid. The third place you can write CSS is inside of an HTML tag, using the style attribute.
Question 19.
Write the HTML code to create the following tables, (i)
(i)
| A | B | C |
| D | E | F |
(ii)
| A | B | C | D |
| E | F | G | H |
Answer:
(i) <html>
<body>
<table frame=”box” rules=”cols”> <tr>
<td> A </td>
<td> B </td>
<td> C </td>
</tr>
<tr>
<td> D </td>
<td> E </td>
<td> F </td>
</tr>
</table>
</body>
</html>
(ii) <html>
<body>
<table frame=”box” rules=”groups”> <tr>
<td> A </td>
<td> B </td>
<td> C </td>
<td> D </td>
</tr>
<tr>
<td> E </td>
<td> F </td>
<td> G </td>
<td> H </td>
</tr>
</table>
</body>
</html>
Section – C
[3 marks]
Question 20.
What is an example of copyright infringement? What is the most common copyright infringement?
Answer:
A typical example of copyright infringement is the use of music in your videos. If you have not obtained the permission to use a song as background music for your home movies, business presentations, or your own creative work, then you could be liable for copyright infringement. Image and text are the two most common types of copyright infringement plagiarism. Whether music lyrics, academic writing, or stock photos, usually using them without informing the owner counts as copyright infringement.
Question 21.
Write a short note on fhe generations of mobile Technologies 3G and 4G.
Answer:
The 3G (Third Generation) systems are also known as Universal Mobile Telecommunications System (UMTS) as they have a single network standard. 3G mobiles use both circuit and packet switched networks. It allows video, audio and graphics applications. Video streaming was introduced. They provide data rates upto 2 Mbps The clarity is more and is close to a real conversation.
• 4G (Fourth Generation) systems provide speed of upto 100 Mbps and prioritize services.
Ex: All resources are allocated to video calls to enhance the quality of the service.
Question 22.
List and explain the different attributes of hr tag?
OR
Ms. Vani, Head Girl of the school, has to display the sequence of events of upcoming school’s Annual Day function on the school website. Help her in writing HTML code to create a table in HTML, as shown in the given screenshot.
| ANNUAL SPORT DAY – SEQUENCE OF EVENTS | ||
| 8:00-9:00 AM | 9:00 AM 1:00 PM | 1:00-2:00 PM |
| OPENING CEREMONY | PRIZE DISTRIBUTION | CULTURAL EVENTS |
Answer:
Specific Attributes
The HTML <hr> tag also supports following additional attributes:
| Attribute | Value | Description |
| align | left right center | Deprecated – Removes the usual shading effect that most browsers display. |
| noshade | noshade | Deprecated – Removes the usual shading effect that most browsers display. |
| size | pixels or % | Deprecated – Specifies the height of the horizontal rule. |
| width | pixels or % | Deprecated – Specifies the width of the horizontal rule. |
OR
<HTML>
<BODY >
<TABLE BORDER = “2” > <TR> <TH COLSPAN= ” 3 ” > ANNUAL SPORT DAY – SEQUENCE OF EVENTS </TH></TR>
<TR ALIGN=”CENTER”> <TD> 8:00 – 9 : 00 AM</TD> <TD> 9 : 00 – 1 : 00 PM</TD>
<TD> 1 : 00 PM – 2 : 00 PM </TD>
</TR>
<TR ALIGN=”CENTER”> <TD> OPENING CEREMONY</TD> <TD>PRIZE DISTRIBUTION</ TD> <TD>CULTURAL EVENTS</TD></TR> </TABLE> </BODY> </HTML>
Question 23.
What are cybersecurity measures? Which tools are used in cyber security?
Answer:
Cybersecurity measures include preventing, detecting, and responding to cyberattacks. Any information stored on an Internet-connected device, computer system, or network can be hacked. With the proper measures in place, this can be prevented.
- Cybersecurity Tools
- Network security monitoring tools.
- Encryption tools.
- Web vulnerability scanning tools.
- Penetration testing.
- Antivirus software.
- Network intrusion detection.
- Packet sniffers.
- Firewall tools.
Section – D
[4 Marks]
Question 24.
Create a web page to demonstrate how to create a link within the same page
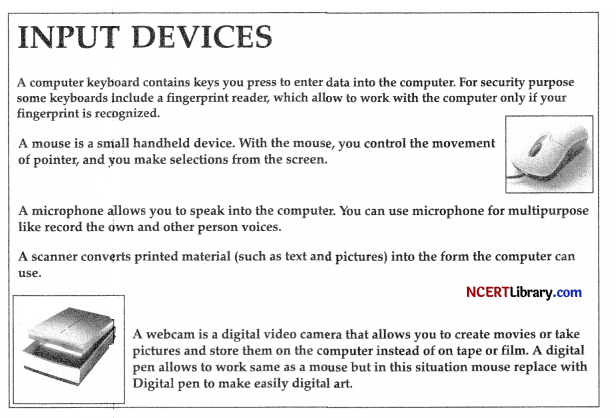
INPUT DEVICES
Write the HTML code to design the above shown web page considering the specifications as given below:
Specification 1: Set highest level heading of words- “INPUT DEVICES”.
Specification 2: .Set image as named – mouse.png and align right.
Specification 3: Set image as named – scanner.png and align left.
Specification 4: write; text in paragraph format
Specification 5: Set picture in border.
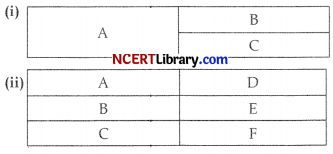
TABLE
Write the HTML code to design the above shown web page considering the specifications as given below: Specification 1: Add two column and two rows in (i) table.
Specification 2: Add rowspan as required in a table.
Specification 3: Add two column and three rows in (ii) table.
Specification 4: add rowspan and colspan if required.
Specification 5: Set value 3 for border line.
Answer:
<BODY>
<H1> INPUT DEVICES </H1>
<P>
A computer keyboard contains keys you press to enter data into the computer. For security purpose some keyboards include a fingerprint reader, which allow to work with the computer only if your fingerprint is recognized.
</P>
<IMG SRC = “mouse.png”align=”right”>
<P>
A mouse is a small handheld device. With the mouse, you control the movement of pointer, and you make selections from the screen.
</P>
<BR>
A microphone allows you to speak into the computer. You can use microphone for multipurpose like record the own and other person voices.
<P>
A scanner converts printed material (such as text and pictures) into the form the computer can use. </P>
<BR>
<IMG SRC = “scanner.png”align=”left” border=”2″>
<P>
A webcam is a digital video camera that allows you to create movies or take pictures and store them on the computer instead of on tape or film.
A digital pen allows to work same as a mouse but in this situation mouse replace with Digital pen to make easily digital art.
</P>
</BODY>
OR
(i) <html>
<body>
<table border=1>
< t r>
<td rowspan=”2″ align=”center”> A </td>
<td> B </td>
</tr>
<tr>
<td> C </td>
</tr>
</table>
</body>
</html>
(ii) <html>
<body>
<table border=”1″ >
<tr>
<td> A </td>
<td> D </td>
</tr>
<tr>
<td> B </td>
<td> E </td>
</tr>
<tr>
<td> C </td>
<td> F </td>
</tr>
</table>
</body>
< / html >
Commonly Made Error:
Student get confused between colspan and rowspan.
Answering Tip:
Stidents must understand the concepts of colspan and rowspan.
Section – E
[4 marks]
![]()
Question 25.
Write the HTML code to generate the following output of a table with content exactly is the same format as shown in the table: Help to complete the table with the right statements in the blanks.
Observe the table and attempt any four questions(out of 5) given after the table:
| ADMNO | SNAME | NAME | DOB | Opening Balance |
| 1110 | MANJIT | RANJIT | 4-MAR-1988 |
<HTML>
<BODY>
<TABLE _____’2″ WIDTH = 500> Statement – 1
<TR ALIGN = “CENTER”_____1 MIDDLE”> Statement – 2
<TH> ADMNO </TH>
<TH> SNAME </TH>
<TH> NAME </TH>
<TH> DOB </TH>
<TH> Opening Balance </TH>
_____ Statement – 3.
<TR
ALIGN = “CENTER” VALIGN = “MIDDLE”>
<TD>_____</TD> Statement – 4.
<TD > MANJIT </TD>
<TD > RANJIT </TD>
<TD > 4-MAR-1998 </TD>
</TR>
_____ Statement – 5
</BODY>
</HTML>
(A) Write the appropriate answer for the blanks given in Statement -1.
(B) Write the appropriate answer for the blanks given in Statement – 2.
(C) Write the appropriate answer for the blanks given in Statement – 3.
(D) Write the appropriate answer for the blanks given in Statement – 4.
(E) Write the appropriate answer for the blanks given in Statement – 5.
Answer:
<HTML>
<BODY >
<TABLE ______= “2” WIDTH = 500> Statement – 1.
<TR ALIGN = “CENTER” = “MIDDLE”> Statement – 2.
<TH> ADMNO </TH>
<TH> SNAME </TH>
<TH> NAME </TH>
<TH> DOB </TH>
<TH> Opening Balance </TH> Statement – 3.
<TR
ALIGN = “CENTER” VALIGN = “MIDDLE”>
<TD>______</TD> Statement – 4.
<TD > MANJIT </TD>
<TD > RANJIT </TD>
<TD > 4-MAR-1998 </TD>
</TR>
______ Statement – 5.
</BODY>
</HTML>
Commonly Made Error
Sometimes students get confused between <tr> and <td>
Answering Tip:
Students must understand the concepts of <tr> and <td>.
Question 26.
MALWARE
’A Melbourne advisory practice was the target of a malware attack, having found malware on their system which locked their access to the platform. The malware allowed the cyber criminal to gain access to an adviser’s login details for all systems he had used recently. The cyber criminals now had access to every website or account that required a login. This included personal banking, platform desktop software, Xplan software and Facebook.
The next time the adviser tried to log in to his platform desktop software, he was locked out. He rang our account executive team to report his access was locked. He couldn’t login, even though he was using his correct user name and password. The platform reset his password. The next day when the adviser tried again to login, he was locked out of the system again.
It became obvious that the adviser’s user ID had been compromised. At this point, the user ID was deleted. Where you have had your platform access locked or you suspect fraud or malware on your system call us immediately as part of your reporting response so we can suspend your login ID to attempt to prevent further fraudulent transactions. Bring in a tech specialist immediately to run and update security software and restore your systems back to normal.
Based on the given information, answer the questions given below. Attempt any four questions:
(A) Is malware as virus?
(B) What are malware attacks?
(C) How does malware spread?
(D) What is the most common malware?
(E) What are the warning signs of malware?
Answer:
(a) Malware is an umbrella term for any malicious software written specifically to infect and harm the host system or its user. A computer virus is just one type of malware. Just as all squares are rectangles (but not all rectangles are squares), all viruses are malware, but not all malware is a virus.
(b) A malware attack is a common cyberattack where malware (normally malicious software) executes unauthorized actions on the victim’s system. The malicious software (a.k.a. virus) encompasses many specific types of attacks such as ransomware, spyware, command and control, and more.
(c) Malware spreads in computer when you download or install an infected software. They also enter your computer through an email or a link. Once malware enters the computer, it attaches itself to different files and overwrites the data. Some malware are to be executed before it’s activated, but some spread immediately.
(d) Viruses. A virus is the most common type of malware attack. In order for a virus to infect a system it requires a user to click or copy it to media or a host.
(e) The following warning signs of malware are:
Your Computer Slows Down.
Your Computer Crashes.
You’re Inundated with Popups.
Unusual Network Activity.