Practicing the CBSE Sample Papers for Class 10 Computer Applications Set 10 allows you to get rid of exam fear and be confident to appear for the exam.
CBSE Sample Papers for Class 10 Computer Applications Set 10 with Solutions
Time Allowed: 2 hours
Maximum Marks: 50
General Instructions:
- This Question Paper has 5 Sections A-E.
- All Questions are compulsory. Hoivever, an internal choice of approximately 30% is provided.
- Section A has 12 questions carrying 01 mark each.
- Section B has 7 Very Short Answer (VSA) type questions carrying 02 marks each.
- Section C has 4 Short Answer (SA) type questions carrying 03 marks each.
- Section D has 1 Long Answer (LA) type question carrying 04 marks.
- Section E has 2 Source based /Case-based /Passage based Questions carrying 04 marks each.
Section – A
(All Questions are Compulsory) [1 mark]
Question 1.
The digital divide separates:
(A) Those who have a computer and those who do not.
(B) Europe and Afric(A)
(C) Those who are computer literate and those who are not.
(D) None of the above.
Answer:
(C) Those who are computer literate and those who are not.
Explanation: The term ’digital divide” refers to the gap between individuals, households, businesses and geographic areas at different socio-economic levels with regard to both their opportunities to access information and communication technologies (ICTs) and to their use of the Internet for a wide variety of activities.
Question 2.
e-Governance is technology that improves?
(A) Accountability
(B) Transparency
(C) Efficiency of government processes
(D) All of the above
Answer:
(D) All of the above
![]()
Question 3.
What is the secured version of File Transfer Protocol?
(A) EFTP
(B) SFTP
(C) SMTP
(D) EMTP
Answer:
(D) EMTP
Question 4.
Servers are computers that provide resources to other computers connected to a:
(A) Client
(B) Mainframe
(C) Supercomputer
(D) Network
Answer:
(D) Network
Explanation: A server is a computer program or device that provides a service to another computer program and its user, also known as the client, which is connected in networking. In a data centre, the physical computer that a server program runs on is also frequently referred to as a server.
Questions 5.
The process of exchanging data packets is called:
(A) Packet Switching
(B) Packet Sharing
(C) Packet Changing
(D) Packet Snatching
Answer:
(A) Packet Switching
Explanation: Packet switching is the transfer of small pieces of data across various networks. These data chunks or “packets” allow for faster, more efficient data transfer. Often, when a user sends a file across a network, it gets transferred in smaller data packets, not in one piece.
Question 6.
What is the term for unsolicited Email?
(A) Spam
(B) Backbone
(C) Usenet
(D) News group
Answer:
(D) News group
Explanation: Spam is; any kind of unwanted, unsolicited digital communication that gets sent out in bulk. Often sparri is sent via email, but it can also be distributed via text messages, phone calls, or social media.
Question 7.
To display (x+y)2, correct HTML code is:
(A) <SUB> (X+Y)2</SUB>
(B) X+Y < SUP > 2 </SUP >
(C) (X+Y) <SUP> 2 </SUP>
(D) <SUP> (X+Y)2</SUP>
Answer:
(C) (X+Y) <SUP> 2 </SUP>
Explanation: The <sup> tag defines superscript text. Superscript text appears half a character above the normal line, and i sometimes rendered in a smaller font.
Question 8.
Which of the following type of HTML tag is used to define an internal style sheet?
(A) <script>
(B) <link>
(C) < class >
(D) < style>
Answer:
(D) < style>
Explanation: <style> tag is used to define an internal style sheet in HTML document.
![]()
Question 9.
Which of the following property is used to increase or decrease the size of a font?
(A) Font-size
(B) Font
(C) Font-variant
(D) Font-weight
Answer:
(A) Font-size
Explanation: The <font> tag in HTML plays an important role in the web page to create an attractive and readable web page. The font tag is used to change the color, size, and style of a text. The base font tag is used to set all the text to the same size, color and face. Syntax: <font attribute = <“value” > Content </font>
Question 10.
Which of the following is not an attribute of < table > tag?
(A) Border
(B) Background
(C) Bgcolor
(D) SRC
Answer:
(D) SRC
Explanation: src – Specifies the path to the image.
Questions No-11 & 12 are Assertion and Reason types. Each question consists of two statements, namely, Assertion (A) and Reason (R). Select the most suitable option considering the Assertion & Reason. DIRECTIONS: In each of the questions given below, there are two statements marked as Assertion (A) and Reason (R). Mark your answer as per the codes provided below:
(A) Both A and R are true and R is the correct explanation of (A)
(B) Both A and R are true but R is not the correct explanation of (A)
(C) A is true but R is false.
(D) A is false but R is true.
(E) Both A and R are false.
Question 11.
Assertion (A): To make a Ordered List we can use <OL> Tag.
Reason (R): To make a Unordered List we can also use <OL> Tag.
(A) Both A and R are true and R is the correct explanation of (A)
(B) Both A and R are true but R is not the correct explanation of (A)
(C) A is true but R is false.
(D) A is false but R is true.
(E) Both A and R are false.
Answer:
(C) A is true but R is false.
Question 12.
Assertion (A): <SELECT> is a container tag. SJIi
Reason (R): Options are placed between two select tags, each with particular VALUE that gets associated with <SELECT>’s name attribute when chosen.
Answer:
(A) Both A and R are true and R is the correct explanation of (A)
Section – B
[2 marks]
Question 13.
What are e-groups? What are the features of E-groups?
Answer:
e-groups are a free email group service that allows us to easily create and join email groups. E-mail groups offer a convenient way to connect with others who share the same interests and ideas. Features of e-groups Creating Folders. Folders are an easy way of organizing files used for various reports and deadlines. Uploading Files. Files have to be added individually by clicking on the ‘Add File’ link and browsing through the computer for the file you wish to upload. Cul/Paste.
Question 14.
What are methods of e-learning?
OR
What are the benefits of e-learning?
Answer:
In this type of learning, E-Courses are made available to the learners in the form of a CD or a Computer-based training (CBT), which can be run on the learner’s system. E- courses can also be made available through Web-based training (WBT), which utilize the internet as a platform like a Learning Management System.
OR
Advantages of e-learning are:
Efficient way of delivering courses as the resources are available from anywhere and at any time; Students can interact with their peers from all around the world through group discussions and private chats; The studying material can be accessed unlimited number of times.
Question 15.
How will you create email link?
Answer:
We can create an e-mail link on web page. The browser will read an e-mail link, using the value Starting with “mailto:” rather than http://, with an e-mail address rather than a web address. The syntax is given below:
<AHREF = “mailto:yourusername@ emailaccountname.com” > E-mail the username </ A>
Question 16.
What social impact dees e-Governance have on society?
OR
What is SCP?
Answer:
(i) Efficiency of administration has increased.
(ii) Reduced cost.
(iii) Corruption has reduced.
(iv) Fast processing
OR
SCP stands for Secure Copy Protocol, which means the user can copy files across SSH connection. That connection will be securely encrypted. It is a very secure way to copy files between computers.
![]()
Question 17.
How can CSS be integrated into an HTML page?
Answer:
There are three ways of integrating CSS into HTML:
using style tags in the head section, using inline-styling, writing CSS in a separate file, and linking into the HTML page by the link tag.
Commonly Made Error:
Students get confused between inline and external css.
Answering Tip:
Students must learn and understand the concept of inline and external css.
Question 18.
Write HTML code to display an ordered list (with uppercase roman number) listing any three subjects being ¦ taught in your school; The web page should have a red background and the title of the page should be “My Subjects.”
OR
Write down the difference between Cell spacing and Cell padding.
Answer:
<html>
<head>
<title> My Subjects </title> </head>
<body bgcolor =”red”>
<ol type = “I”>
<li> Science. </li>
<li> Maths </li>
<li> Computers </li>
</ol>
</body>
</html>
OR
Cellspacing: This attribute is used to set the minimum distance between two adjacent cells, cellspacing is the number of pixels between the table cells.
Cellpadding: This tag sets the margin within a cell, it is the pixel space inside the cells, i.e. the distance between the cell content and the cell boundary.
Commonly Made Error:
Students get confused between cellspacing and cellpadding.
Answering Tip:
Students must learn and understand the concept of cellspacing and cellpadding.
Question 19.
Write code to create a login screen.

Answer:
<form>
<fieldset>
<legend>Log In</legend>
<label>Username: cinput type=”text”></labels>
<BR>
<label>Password: <input
type=”password”></label>
<BR>
<input type=”submit” value=”Submit”> </fieldset>
</form>
Section – C
[3 marks]
Question 20.
What are the 4 types of plagiarism? Is plagiarism a crime?
Answer:
he Common Types of Plagiarism
Direct Plagiarism. Direct plagiarism is the word-for- word transcription of a section of someone else’s work, without attribution and without quotation marks.
Self Plagiarism.
Mosaic Plagiarism.
Accidental Plagiarism.
Plagiarism is the act of taking a person’s original work and presenting it as if it was one’s own. Plagiarism is not illegal in the United States in most situations. Instead it is considered a violation of honor or ethics codes and can result in disciplinary action from a person’s school or workplace.
Question 21.
What is the meaning of uploading? Give some guidelines for safe downloads.
Answer:
Uploading is the transmission of data or file from a local computer to a remote computer, as .from-‘ your PC to a website you are constructing. It allows users to easily exchange files over networks. While downloading any file close all the applications that are running on your computer, let only one set-up file run at a time of downloading. Close all the important applications in order to be safe if something goes wrong while downloading.
Set firewalls, and antivirus to actively scan all the files you download. Scan all the files after you download whether from websites or links received from e-mails. Always use updated antivirus, spam filter and spyware to help detect and remove virus, spyware from the application you want to download.
Question 22.
What are the limitations of CSS?
OR
Name media types allowed by CSS.
Answer:
CSS cannot always assure compatibility with every browser; you need to be cautious while choosing the style selector. The parent selector tag is not available, thus you can’t select the parent selector tag. Some selectors can lead to cross-browser issues due to their less browser-friendly behaviour. We cannot request a webpage through CSS.
OR
The different media types allowed by CSS are:
speech
audio
visual
tactile media
continuous or paged media
grip media or bitmap
interactive media
![]()
Question 23.
Mr. Ayus is studying cyber security. You, being his friend explain the concept of software piracy?
Answer:
Software piracy is any attempt to break the licence terms of a piece of software. This includes downloading and using a program without paying for it, as well as buying, selling or giving away illegitimate copies of a game or any other piece of software. It could mean extracting code from a program, or modifying it without permission in order to do something that the developers did not wish you to do. When you buy software, music or films legally, copyright law forbids us from:
- giving a copy to a friend
- making a copy and then selling it
- using the software on a network (unless the licence allows it, eg it is a business licence)
- renting the software without the permission of the copyright holder The practice of copying software is a serious problem in some countries. Copying music, films and software illegally means that there is less money available to pay the writers, developers and artists.
Section – D
[4 Marks]
Question 24.
Carefully study the Web page given below. Identify 10 tags (structural as well as formatting tags) that have been utilized in creating this Web page and write the usage of each of them.

OR
Write the HTML code to design the web page as shown below, considering the specifications that follow. You can write code for any 4 specifications out of the given 5 specifications:
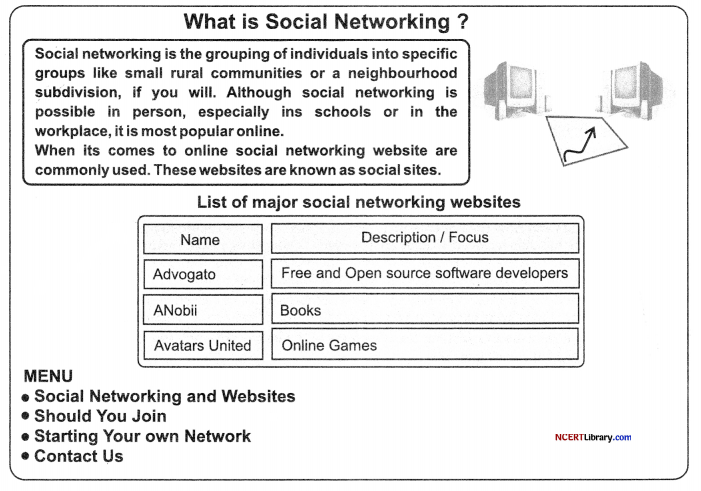
Specification-1: Title of the web page is “Social Networking” and the heading of level -1 at the middle of the web page is “What is Social Networking ?”.
Specification-2: The caption of the table is “List of major social networking websites”
Specification-3: The tabular data of 4 rows and 2 columns is with border size as 2 and the gap between the cells 2.
Specification-4: Insert the picture named “comp.jpeg”.
Specification-5: create the unordered list of different menus.
Answer:
(a) <title > to specify the title of the Web page.
(b) <body> contains all the content that is to be displayed on the Web page and all the various formatting and structural tag.
(c) <ul> used to create an unordered list.
(d) <li> to specify the various list items in a list.
(e) <caption> to provide caption to the table.
(f) < table > used to create table in HTML document.
(8) <tr> stands for table row, used to create a table row.
(h) < td > stands for table data, helps to create cells in HTML table.
(i) <img> used to insert an image in HTML document.
(j) <a> stands for anchor tag. Use the href attribute to provide the reference of the Web page that you want to hyperlink.
OR
<HTML> <HEAD> <TITLE>Social
Networking</TITLE> </HEAD>
<BODY BGCOLOR=”Pink” LINK=”Green”
ALINK=”Blue” VLINK=”Red”>
< CENTER > < HI > < FONT COLOR
z=”maroon” > What is Social Networking?
</FONT> </Hl > </CENTER> <IMG
SRC=”comp.jpeg” ALIGN=”right” HEIGHT=125
WIDTH=250> <FONT COLOR=”purple”
SIZE=5>
Social networking is the grouping of individuals into specific groups like small rural communitiesor a neighbourhood subdivision, if you will.
Although social networking is possible in person, especially in schools or in the workplace, it is most popular online.
</FONTxP> <FONT COLOR=”black” SIZE=5> When it comes to online social networking, websites are commonly used.
These websites are known as social sites.
</FONT><P> <CENTER> <TABLEBORDER=2 BORDERCOLOR=”blue” CELLSPACING=5 > <FONT COLOR=”BLUE” >
<CAPTION> List of major social networking websites</CAPTIONxTR> <TH> Name </ TH > < TH > Description / Focus </TH > </TR > <TR> <TD> Advogato</TDxTD> Free and Open source software developers </TDx/TR> <TR> <TD> ANobii </TDxTD> Books </TDx/TR>
<TR>
<TD> Avatars United </TDxTD> Online Games </TD> </TR> </TABLEx/CENTER> <BR>
< UL xLI x A HREF=”one.html” > Social Networking and Websites </A> <LI>
<A HREF=”two.html”>Should You Join</A> <LI> <A HREF=”three.html”>Starting Your own Network</A> <LI> <A HREF=”mailto:abc@ xyz.com”>Contact Us</A> </UL>
</BODY >
</HTML>
Commonly Made Error:
Students get confused between inline and external css.
Answering Tip:
Students must learn and understand the concept of inline and external css.
Section – E
[4 marks]
Case Study-1
Question 25.
Ayus went to an interview for the post of web developer. In the technical test, he was supposed to design an HTML table as given below. Help him to complete the table with the right statements in the blanks. Observe the table and attempt any four questions (out of 5) given after the table).
| FIRST NAME | LAST NAME | EMAIL ADDRESS |
| Hillary | Nyakundi | tables@mail.com |
| Lary | Mak | developer@mail.com |
<table ______=1> <!-STATEMENT-1>
<_______> <!-STATEMENT-2>
<th>First Name</th>
<th>Last Name</th>
<______>Email Address<______> <!-STATEMENT-3>
</tr>
<tr>
<td>Hillary</td>
<td>Nyakundi</td>
<td>tables@mail.com</td>
</ tr>
<tr>
<______>Lary<______> < ! – STATEMENT – 4 >
<td>Mak</td>
<td>developer@mail.com</td>
</tr>
<______> <!-STATEMENT-5>
(a) Write the attribute value to complete Statement-1 to achieve the output given in the above table.
(b) Write suitable tag for the blanks given in Statement-2.
(c) Write the appropriate answer for the blank given in Statement-3
(d) Write the appropriate answer for the blank given in Statement-4
(e) Write the appropriate answer for the blank given in Statement-5
Case Study-2
Answer:
(a) border
(b) <tr>
(c) < th> Email Address </th>
(d) <td>Lary</td>
(e) </table>
Question 26.
Sara, age 14, had sent some ‘dirty’ photos to her 15-year-old boyfriend through Snapchat. He has shown the photos to his friends and now the boys are making fun of her. They are calling her names as she walks by them in the hallway. She has also received 13 Snapchat messages requesting naked pictures of her. The principal and the teachers have not reacted yet but plan to discuss the incident during the teachers’ conference next month. None of the other students have been approached about the incident so far.
When Sara reported the incident, the school counsellor took notes of her statement. Since Snapchat deletes shared content after it has been viewed, no record of either the photo or the messages exists. Baed on the given information, answer the questions given below. Attempt any four questions:
(a) Identify the type of cybercrime Sara is a victim of.
(b) After hearing about his ordeal, the school decides to publish a set of moral principles that determines the appropriate behavior of students while using the IM. The school is referring to
(c) Write a safety measure to be taken by sara to avoid threats from all this unknown people in the future.
(d) sara decides to make a list of common safety precautions to be taken when online. Write any two points that sara should include in his list.
(e) Why are privacy settings so important in Instant Messaging Application?
Answer:
(a) Sara is a victim of cyber bulling,
(b) cyber bulling awareness.
(c) Sara can block all this users.
(d) Make the most of privacy settings. Investigate what measures you can take to keep content private on the websites you use. Think before you post. Never forget that the internet is public. Keep personal information personal.
(e) Public Instant Messaging transmits unencrypted information, so it should never be used for sensitive or confidential information. The information is on the Internet and may be accessed by anyone.